Privacy-Conscious Query Authentication for Outsourced and Cloud Databases
Project Team: Prof. XU, Jian Liang |
 |
Abstract: |
|
In data oursourcing, it is critical for a query client to be able to authenticate the result of a query from the outsourced server, in terms of both soundness and completeness. However, existing works assume that during the authentication process, the client can always be trusted and entitled to receive data values on the querying attribute(s), even if they are not the results. This severely jeopardizes the privacy of the data owner. In this project, we study authentication for such a privacy-conscious query model where the querying attribute(s) are unavailable to the client. |
Case Study: |
|
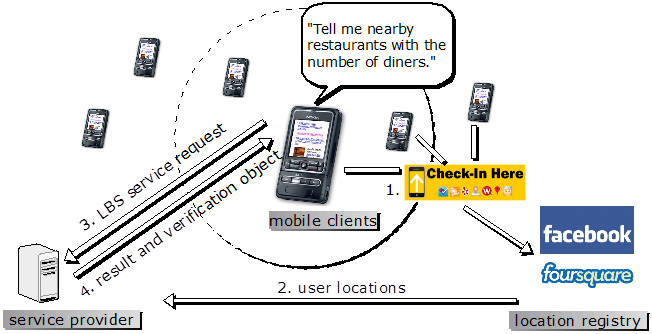
As more mobile users like to "check-in" at restaurants or other hotspots, geo-social network portal such as Facebook or Foursquare has a large number of user locations. Third-party application use these check-in locations to provide query service like "which restaurant has the most diners". To ensure the querying user receives the genuine result, we design an authentication framework without disclosing check-in locations to the querying user.
|
|
Problems and Methodology: |
- Privacy-Conscious Authentication for Single Selection Queries
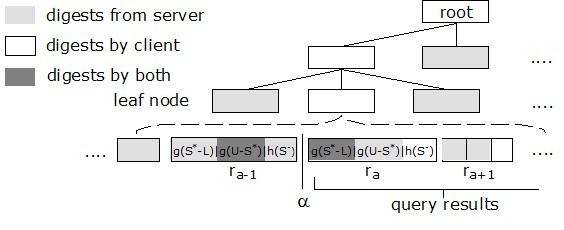
Given table T whose schema consists of fields T(S1, . . . , Sd) with domains D1, . . . ,Dd, the query is a selection on S* with predicates [α, β] and a projection on S-, where S* are the sensitive field(s) and S- are the projection field(s). The objective is to design authentication protocols, together with the authentication data structure (also known as the verification object or VO) without disclosing to the client any attribute values from the sensitive fields S*. The rationale of authentication is to let the client and server jointly restore some values --- g() function values --- based on S* that are pre-signed by the data owner.
- Authentication for Multi-dimensional Range Queries
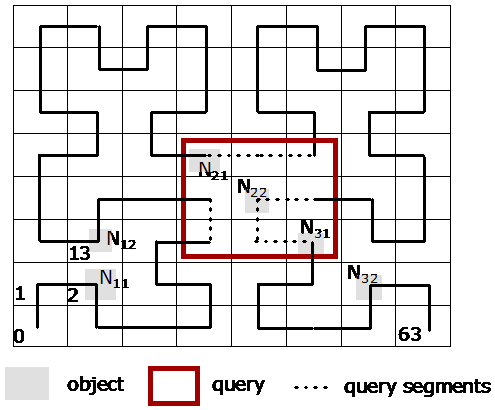
We extend the querying attribute(s) S* from a single field to multiple fields. Then the query becomes a multi-dimensional range query. The challenge is that objects are no longer linearly sorted by their S* values at the leaf level of the index. A possible solution is to reduce the dimension by some space filling curve (e.g., a Hilbert curve as illustrated below).
|
Publication |
- Q. Chen, H. Hu, and J. Xu. "Authenticating Top-k Queries in Location-based Services with Confidentiality." Proceedings of the VLDB Endowment (PVLDB '14), accepted to appear.
- X. Lin, J. Xu, H. Hu, and W.-C. Lee. "Authenticating Location-Based Skyline Queries in Arbitrary Subspaces." IEEE Transactions on Knowledge and Data Engineering (TKDE), accepted to appear.
- H. Hu, Q. Chen, and J. Xu. “VERDICT: Privacy-Preserving Authentication of Range Queries in Location-based Services” Proc. of the 29th IEEE International Conference on Data Engineering (ICDE '13), demo paper, accepted to appear.
- H. Hu, J. Xu, Q. Chen, and Z. Yang. “Authenticating Location-based Services without Compromising Privacy.” Proc. of the 2012 ACM SIGMOD International Conference on Management of Data, pp. 301 – 312.
- X. Lin, J. Xu, H. Hu. "Authentication of Location-based Skyline Queries." Proc. of the 20th ACM Conference on Information and Knowledge Management (CIKM '11), short paper.
|
Patent Application |
- H. Hu, J. Xu, and Q. Chen. "Method and Apparatus for Authenticating Location-based Services without Compromising Location Privacy." US Non-Provisional Patent Application No. 13/769,846.
|
|
For further information on this project, please contact Prof. XU, Jian Liang.
|