Big Data Analytics and Management (BDAM)
The BDAM research group aims to facilitate secure, effective, and efficient use and management of big data under a wide variety of hardware, software, and organizational settings. The research topics include data analytics, blockchain, databases, data privacy and security, query processing, and graph/social/spatial data management.
Faculty Involved:
Funded Research and Consultancy Projects in the Past Few Years:
| Exploratory Search on Graph Databases through Subgraph Query Feedback |
 | Staff |
Dr. CHOI, Byron Koon Kau |
| Abstract |
- To formally analyze the feedback (WIFSSQ and WNSSQ) and propose novel querying algorithms
- To efficiently integrate the feedback as a generic module into a GUI for graph platforms
- To formulate the optimal opportunities for delivering feedback
- To conduct comprehensive performance and usability evaluations
|
| Privacy-preserving Linear Algebra Framework for Graph Query Algorithms for Massive Networks |
 | Staff |
Dr. CHOI, Byron Koon Kau |
| Abstract |
- To study a set of linear algebra operators such as set intersection/union, scalar product, matrix multiplication/addition, and propose the encoding and encryption for graph queries
- To apply privacy-preserving optimizations for the specific algebra operations
- To unify the operations and develop a publicly available tool (API)
|
| Efficient Graph Search Algorithms for Public-Private Social Networks |
 | Staff |
Dr. HUANG, Xin |
| Abstract |
- To design public-private graph models, and collect real-life public-private graph datasets;
- To investigate efficient algorithms of community search and keyword search on public-private networks;
- To develop a prototype system to demonstrate the feasibility of public-private social network analysis;
|
| Keyword-Centric Community Search |
 | Staff |
Dr. ZHANG, Zhiwei |
| Abstract |
- To formally analyze the differences and benefits of a new framework based on graph contraction compared to existing frameworks.
- To design new algorithms for basic graph operations, including node centric graph operations and edge centric graph operations.
- To efficiently integrate these developed basic graph algorithms for graph applications.
|
| Development and Evaluation of the Effectiveness of an Online Cognitive Behavioral Intervention Program for Hong Kong People with Social Anxiety Disorder |
 | Staff |
Prof. XU, Jianliang |
| Abstract |
- To develop an online Cognitive Behavioral Therapy (CBT) program (including both an online platform and mobile application) for Hong Kong people with Social Anxiety Disorder
- To evaluate the effectiveness of this online CBT program in reducing anxiety symptoms and psychological distress, and improving quality of life for Hong Kong people with Social Anxiety Disorder at post-treatmentMore
- To evaluate the maintenance effects of this online CBT program at 3- and 6-month follow-up tests
- To test the predictive effects of sociodemographic factors (e.g. age, education, marital and economic status) in the treatment effects
|
| ImageProof: Enabling Authentication for Large-Scale Image Retrieval |
 | Staff |
Prof. XU, Jianliang |
| Abstract |
- To design novel frameworks and query authentication algorithms for the verification of large-scale image retrieval.
- To propose novel ADSs and several optimization techniques for robust and efficient authenticated top-k image queries.
- To evaluate the proposed techniques by combining theoretical analysis and empirical experiments.
|
| Towards Searchable and Verifiable Blockchain |
 | Staff |
Prof. XU, Jianliang |
| Abstract |
- To design a framework for blockchain to alleviate the storage and computing costs of the user and support verifiable Boolean range queries to guarantee the results’ integrity.
- To design an efficient index structure that supports range queries with integrity assurance in a hybrid-storage blockchain
framework.
|
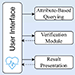
| Verifiable Attribute-Based Search over Shared Cloud Data |
 | Staff |
Prof. XU, Jianliang |
| Abstract |
- To design novel security primitives for supporting verifiable attribute-based access control over shared cloud data.
- To protect data content and access policy of outsourced databases in a zero-knowledge manner.
- To propose query authentication algorithms and optimization techniques for various query types.More
- To develop a demonstration system to show the robustness and efficiency of our proposed techniques.
|












